THE CONTEXT- A recently published report by Moody’s, a U.S.-based global credit rating agency, has flagged serious concerns about security and privacy vulnerabilities in the Aadhaar, India’s ambitious digital identification programme for residents. The report titled, “Decentralized Finance and Digital Assets”, appreciated the scale and innovative nature of Aadhaar but red-flagged risks from using “centralised” digital ID systems which often lead to exclusion of beneficiaries and denial of entitlements and services promised under welfare schemes by the government.
WHAT IS AADHAAR?
- Aadhaar number is a 12-digit random number issued by the UIDAI (Unique Identification Authority of India) to the residents of India after satisfying the verification process laid down by the Authority. Any individual, irrespective of age and gender, who is a resident of India, may voluntarily enrol to obtain Aadhaar number.
- The enrolment process is cost-free and requires a person to provide minimal demographic and biometric information such as ten Fingerprints, two Iris Scans, and facial photograph.
- Aadhaar enrolment is done through existing public and private infrastructure.
- While a Central Identities Data Repository (CIDR) is managed by the UIDAI, ‘Registrars’ who handle enrolment through authorised connections to the CIDR, are UIDAI partners.
- The objectives of UIDAI were to ensure that all residents have a unique ID and to curb corruption in accessing welfare programmes by eliminating “ghost” and “fake” individuals. This is ensured through Aadhar-seeding with the welfare schemes whereby the government linked the database of beneficiaries with the Aadhaar database.
- India is not the only country to have adopted a foundational identity system; countries such as Sweden, Argentina and Nigeria also have similar digital ID schemes in place.
EVOLUTION OF AADHAAR IN INDIA:
2006
Unique Identify (UID) Scheme for poor families was approved by the Ministry of Communications and Information Technology.
2007
The need for creation of a residents’ database was underscored by the Empowered Group of Ministers.
2010
National Identification Authority of India Bill, 2010 was introduced in the Parliament.
2011
Standing Committee on Finance rejected the Bill and recommended the need for a legislation to protect privacy and data of the individuals.
2013
An interim order was passed by the Supreme Court (SC) stating that no person should suffer from not having Aadhaar.
2015
A 3-Judge SC Bench limited the use of Aadhar for certain welfare schemes.
2016
Aadhar (Targeted Delivery of Financial and Other Subsidies, Benefits and Services) Bill was introduced as Money Bill in the Parliament which received the Presidential assent
2017
Aadhar was made mandatory by the Central government for welfare, pension and employment schemes as well as for filing the Income Tax Returns (ITR).
2018
5-judge Constitutional Bench having heard 30 petitions challenging validity of the Aadhar, upheld its validity.
Ruled out the need for Aadhar to open a bank account, get a SIM card or school admissions, or to take examinations etc.
KEY HIGHLIGHTS OF THE REPORT:
Issues stemming from Centralised Digital ID systems:
- Aadhaar touted as the world’s largest digital ID program, assigns unique numbers to over 1.3 billion Indian residents using biometric and demographic data.
- Verification through biometrics and OTPs allows the beneficiaries to access various public and private services. However, Moody’s highlighted the centralised control of Aadhar data by the government through the UIDAI and the potential misuse or exploitation of personal data by a ‘Surveillance State’.
- This violates the fundamental right to privacy enshrined under Article 21 of the Indian Constitution and the landmark Puttaswamy Judgement of the apex court of India.
Privacy & Security Concerns
- Since Aadhaar and its seeding with various welfare schemes and public services is built on enormous sensitive data, it is often susceptible to data breaches and data theft.
- The concerns of security and privacy are rooted in the lack of adequate data protection legislation and growing cyberattacks from adversaries, through Dark Net.
Case study- Cyble, a global cyber intelligence agency, in June 2020, highlighted the issue of sale of sensitive data such as Aadhar data, PAN cards etc. on the Dark Web. Cyble hinted at probable leakage of such sensitive data by the private/third party agencies having access to personal data of individuals in the country.
- Sensitive data, such as biometrics, carry a high risk of exploitation. For instance, biometrics can be exploited through “man-in-the-middle” attacks, where attackers gain access to biometric data that they can misuse to access an individual’s financial resources. This is especially concerning in the case of marginalized communities.
Concerns due to Biometric Authentication
- The denial of services to beneficiaries of various welfare schemes such as MGNREGA, PDS, etc. due to difficulties in Aadhar biometric authentication is one of the concerns.
- The labourers from hot, humid climates and manual labourers whose fingerprints are susceptible to change or fade over time, face denial of services/entitlements under MGNREGA, PDS or subsidy schemes.
- The texture of fingerprints alters according to the climate. For instance, in humid climate, fingers become saturated and wrinkled, resulting in acquisition of fingerprints of degraded accuracy.
- On the other hand, hot and arid climate leads to skin dryness, posing challenges for fingerprints authentication. Dry, non-pliable skin fails to lay flat on sensors, preventing the ridges from making sufficient contact. As a result, the resultant fingerprint quality is compromised.
- The failures in authentication in many cases, has also resulted into cancellation of legitimate beneficiary names from some welfare schemes.
Case study of Jharkhand (2021)- People were refused support under PDS due to biometric failure and other technological Aadhar glitches. This led to starvation and death of some people.
WHAT HAS BEEN THE GOVERNMENT’S RESPONSE TO MOODY’S REPORT ON AADHAR?
The Indian government held the Moody’s findings as baseless and has reassured confidence in the Aadhaar technology and system. The Moody’s report lacked sufficient reasons and evidence (primary or secondary data or research) to back its findings; hence, its findings have no substance.
- DBT payments under MGNREGA: The Government of India stressed that as far as the question of deniability of services and payments to workers under MGNREGA was concerned, the government has in place the system of DBT wherein the money is directly credited to the accounts of the labourers, and this does not require the worker to authenticate using their biometrics.
- Alternatives to Biometrics in place: Moody’s has ignored that biometric submission is also possible through contactless means like face authentication and iris authentication. In addition, the option of mobile OTP is also available in many use cases.
- Internationally applauded and Recognised system: Recently, the G20 Global Partnership for Financial Inclusion (GPFI), in a report prepared by the World Bank, appreciated the implementation of Digital Public Infrastructure (DPI) such as Aadhaar along with the Jan Dhan bank accounts, and mobile phones, which played a critical role in moving ownership of transaction accounts from approximately one-fourth of adults in 2008 to over 80% now.
In the absence of Aadhar and supporting services, this journey would have taken up to 47 years.
- Safety measures introduced by the UIDAI: Virtual Aadhar is a revocable temporary 16-digit random number linked to the Aadhaar number. When executing authentication or e-KYC services, VID can be utilised instead of Aadhaar number. The UIDAI has warned the “general public not to share photocopy of one’s Aadhaar with any organisation, because it can be misused”. Instead, it recommended that “a masked Aadhaar, which displays only the last four digits of your Aadhaar number,” be used for such purposes.
DECENTRALISED DIGITAL IDs as an Alternative Solution:
Moody’s Report having criticised the centralised Digital IDs such as Aadhar, pitched the concept of Decentralised Digital IDs as an alternative solution. Moody’s emphasises that although DID systems are still in their early stages of development, they hold substantial potential to offer a more robust and private avenue for managing digital identities.
- Decentralized ID systems (DIDs) use cryptography, digital wallets and related technologies to enable multiple entities to contribute credentials and empower individuals to manage their data.
- Unlike traditional systems, DID allows individuals to own and control their digital credentials.
- In DID, a person’s personal data is securely stored in their digital wallet, and the process of verifying their identity does not rely on a single, centralized institution.
- Instead, it occurs on a decentralised digital ledger, such as a blockchain which makes it more secure and reliable compared to the centralised systems such as Aadhar.
- Instead of entrusting a third party to store, manage and transmit data on their behalf, individuals can use decentralized ID systems to exchange credentials directly with one another or a service provider. This helps in reducing the number of intermediaries and increasing efficiency.
- Decentralized ID systems may also enhance effectiveness by reducing the number of times information has to be verified, which could increase convenience, reduce risk and diminish costs.
CHALLENGES ASSOCIATED WITH DECENTRALISED DIGITAL IDs:
- Political risks: While decentralized ID offers a way for individuals to exercise greater control over their personal data, depending on its use context, it could still contribute to polarization. Digital IDs issued by social media companies can contribute to political polarization by reinforcing group identities.
- Data Security Risks: Although decentralized ID aims to minimize data collection and data storage, it still risks increasing the collection of sensitive personal data, opening the possibility of theft or leakage.
- Nascent Stage: DID systems are still in their early stages of development. Therefore, the associated policies, regulations and standards are lacking.
DIFFERENCES BETWEEN CENTRALISED AND DECENTRALISED DIGITAL IDs:
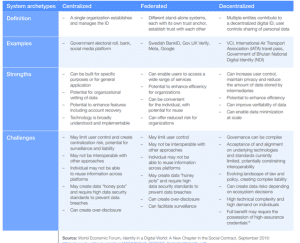
FINANCIAL SAVINGS due to AADHAR SEEDING:
About 300 schemes of the Central Government and 400 schemes of state Governments have been linked with Aadhaar. The Aadhar-seeding has helped the government in weeding out about 6 crore fake and duplicate beneficiaries due to which savings worth Rs.90,000 crore have been reported as per the UIDAI.
WAY FORWARD:
In order to address the challenges associated with digital IDs such as Aadhar etc., the following measures must be taken into account:
- Robust Data Protection Framework: FATF recommends that digital ID be accompanied by the development of robust, fit-for-purpose regulations. For instance, the General Data Protection Regulation (GDPR) implemented by the European Union in 2018 which applies to all organisations that process the personal data of EU citizens, regardless of the location of the organisation. Individuals are given the right to access, rectify and erase their personal data as well as the right to data portability.
KS PUTTASWAMY JUDGEMENT (2017):
A nine-judge bench of the Supreme Court in Justice K. S. Puttaswamy (Retd.) Vs Union of India unanimously held that the constitutionally protected fundamental right to privacy is an intrinsic part of life and liberty under Article 21.
Therefore, having a robust and comprehensive legislation aimed at protecting the sensitive personal data such as Aadhar, is imperative for ensuring the privacy and security of residents in the country.
- Cybersecurity Augmentation: FATF recommends that government and industry keep pace with technological change by encouraging stakeholder engagement, use of blockchain and cryptography, developing technical and cybersecurity expertise to improve data management, and attempting to educate and raise awareness of the potential of these technologies.
- Decentralised Data Control and Access: As argued by the Moody’s, a person’s personal data is securely stored in their decentralised digital wallet built using blockchain and big data. Also, the process of verifying their identity does not rely on a single, centralized institution. The individuals whose data is being stored and processes must be given effective say in the collection, storage and deletion of data, especially the sensitive personal data like biometrics.
THE CONCLUSION- For an ID system to work for the citizens of a country, accountability and transparency must also be built into the system through meaningful consultations, independent audits and effective grievance redressal. A well-designed system, with adequate safeguards in place, can facilitate civic empowerment and inclusion, unlocking significant economic value.
MAINS PRACTICE QUESTIONS:
Q. Differentiate between centralised and decentralised digital IDs. Also, analyse the weaknesses in the centralised digital IDs.
Q. The centralised digital IDs pose some security and privacy challenges which can be overcome with adoption of decentralised Digital IDs. Comment.
Spread the Word



