THE CONTEXT: In November 2022, the premier medical institute in the country, All India Institute of Medical Sciences New Delhi (AIIMS) was crippled by a major cyberattack. Most of its servers stopped working as also the eHospital network. All functions including the emergency, out-patient, in-patient and laboratory wings had to be shifted to manual management. This article discusses the issue of cyberattacks, especially on Critical Information Infrastructure in detail.
RANSOMWARE ATTACK ON AIIMS
DEVELOPMENTS SO FAR
- On 23 November 2022, patients and doctors complained about the hospital’s services working slowly or not at all. As a result, the hospital was forced into working in a manual mode.
- The National Informatics Centre investigated the issue and found signs of a ransomware attack on the hospital’s servers.
- The attack corrupted all the files stored on the main and backup servers of the hospital.
- The cyber attack derailed many day-to-day activities at AIIMS, with OPD registrations and blood sample reports being halted at the premier institute. While AIIMS was able to restart some of these services, records were being kept manually causing delays and inconvenience to medical personnel and patients alike.
- The breach in security has particularly affected the e-hospital application, which was provided and managed by NIC since 2011-12, stopping the online functioning of OPD, emergency, and other patient care services on the AIIMS premises.
- On 30 November 2022, AIIMS decided to get four new servers from the Defence Research and Development Organisation (DRDO) so it can resume its e-hospital facility for patients.
- On 16 December 2022, Replying to another question in the Lok Sabha, Minister of State for Health and Family Welfare said
o All the data for e-Hospital had been retrieved from a backup server and restored on new servers.
o Most of the functions of e-Hospital application such as patient registration, appointment, admission, discharge etc. had been restored after two weeks of the attack.
- Probe agencies have still not located the person, organisation and exact physical location linked to the cyberattack. However, they have tracked a server address in China, which could be an indication towards state sponsored cyber warfare which was already flagged by various cyber threat intelligence firms.
IMPACTS AND RAMIFICATIONS
- The organisation’s critical data is encrypted so that they cannot access files, databases, or applications stored on the main and backup servers of the hospital.
- The cyberattack has frozen everyday work at AIIMS, including appointments and registration, billing, laboratory report generation, etc.
- The exploited databases also contained personally identifiable information of patients and healthcare workers — and administrative records on blood donors, ambulances, vaccination and caregivers, and employee log-in credentials.
- The data breach has reportedly compromised the data of nearly 3–4 crore patients, including sensitive data and medical records of several VIPs including former prime ministers, ministers, bureaucrats, and judges,
RESPONSE OF SECURITY AGENCIES
Multi-agency investigation: The extent and threat of the attack was so much that multiple agencies like Delhi Police, the Centre’s Computer Emergency Response Team (CERT-In), the Ministry of Home Affairs, and even the National Investigation Agency have joined the probe.
- A case of extortion and cyber terrorism was registered by the Intelligence Fusion and Strategic Operations (IFSO) unit of the Delhi Police since the attackers made an undisclosed (allegedly Rs. 200 Crore) demand to be sought in cryptocurrency in exchange for a key that would decrypt the data.
- The Delhi Police’s use of the provisions of section 66 (F) of the Information Technology Amendment Act 2008 identifying this incident as a case of cyber terrorism is significant and indicates a much larger ambit than a typical ransomware case.
- The Computer Emergency Response Team (CERT-In) and National Informatics Centre worked on the hospital’s servers to restore functionality.
FINDINGS
- CERT-In, the country’s premier cybersecurity agency, has found that the hackers had two Protonmail addresses – “dog2398” and “mouse63209”.
- They also found that ‘dog2398’ and ‘mouse63209’ were generated in the first week of November 2022 in Hong Kong. They also found that another encrypted file was sent from China’s Henan.
- The targeted servers were infected with three ransomware: Wammacry, Mimikatz and Trojan.
- The investigation also revealed that the main server and applications responsible for OPD services were down as all the system files in the home directory were encrypted by changing their extension to .bak9 – a new file that encrypted the extension files of the system.
- As per CERT-In’s preliminary diagnosis, the cyberattack was the result of an “unorganised ICT (information and communications technology) network without centralised monitoring or system administration”.
- This means the infected devices were connected to each other and the data on all of them could be accessed from every connected device — and no team was monitoring who was accessing these systems.
CYBERATTACK ON CRITICAL INFORMATION (CI) INFRASTRUCTURE
Cyber attacks on medical institutes are getting common, and the pandemic has been a turning point as hackers and criminal syndicates realised the dependence of these institutes on digital systems, to optimally manage medical functioning as well as store and handle large volumes of patient data, including their medical reports. In such a situation, both the aspects of security and privacy surface. Hence most countries define the health and medical sector as Critical Information (CI) Infrastructure.
In India, while health is not specified directly as a CI, an organisation like AIIMS New Delhi could be counted as a “strategic and public enterprise” as it treats crores of patients, including the top leadership of the country. It also handles and stores very sensitive medical research data. It is a natural target for cyber attackers and ransom seekers because the data available here is more precious than even oil.
The ransomware attack on AIIMS is the first such attack on an Indian healthcare institution even as such institutions have been a favoured target of ransomware over the past few years.
- The Information Technology Act of 2000 defines “Critical Information Infrastructure” as a “computer resource, the incapacitation or destruction of which shall have debilitating impact on national security, economy, public health or safety”.
- The government, under the Act, has the power to declare any data, database, IT network or communications infrastructure as CII to protect that digital asset.
SECURITY INCIDENTS IN CRITICAL INFRASTRUCTURE IN INDIA
India has witnessed at least seven major cyberattacks and security incidents in critical infrastructure companies in the last two years and most of them have been in 2022. While there have been security incidents and attacks on critical assets in the past, the frequency, scale, and impact of recent episodes have demonstrated just how close adversaries have gotten to causing irreversible damage.
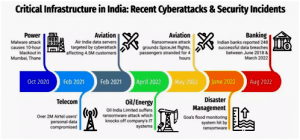
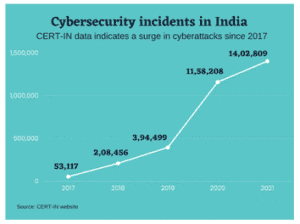
The Indian Computer Emergency Response Team (CERT-IN) in its India Ransomware Report 2022 stated that there is a 51-percent increase in the number of ransomware attacks across multiple sectors including critical infrastructure.
THE ANALYSIS:
Though India has been paying greater attention to cyber security, the rising number of attacks on India should be very worrying to Indian security managers. A more worrying aspect of the cyber attack is that it is not an isolated incident. In fact, the number of cyber attacks on healthcare infrastructure has gone up significantly in recent years.
Cloud SEK, an AI company that has been monitoring cyber threats, noted in a report that the Indian healthcare sector was second in terms of the number of attacks, accounting for 7.7 percent of the total attacks on the healthcare industry worldwide in 2021, and 29.7 percent of all attacks in the Asia-Pacific region. This is a consequence of the greater digitalisation taking place, especially in the context of the COVID-19 pandemic. The study also said that the number of cyberattacks against the healthcare industry has increased by 95.34 percent in the first four months of 2022 as compared to the number of cyberattacks in 2021 during the same period.
While the healthcare industry has become a particularly attractive target for hackers and criminals, cyberattacks on other sectors in India have been equally critical. The number of incidents involving data breaches and digital banking threats has been on the rise, exposing Indian vulnerabilities in the cyber security domain.
Whether these attacks lead to data or financial loss or not, the more serious issue is the ability of the perpetrators to crack the Indian cyber security system, despite India’s security efforts. They also reflect the still-inadequate protection measures afforded to critical information infrastructure in India.
CYBER SECURITY ARCHITECTURE IN INDIA
LEGAL FRAMEWORK
INFORMATION TECHNOLOGY ACT,2000
v The provisions of the IT Act deal with evidentiary value of electronic transactions, digital signatures, cyber-crimes, cyber security and data protection.
v It intends to give legal recognition to e-commerce and e-governance and facilitate its development as an alternate to paper based traditional methods.
OTHER LAWS
v Apart from IT Act 2000 there are other laws as well that govern and regulate cyberspace.
v For online contracts- Indian Contracts Act, Sale of Goods Act 1930 etc would define legality as well
v Provisions of Competition Act 2002 and Consumer Protect Act 1986 are also relevant for cyber space
v Indian Copyright Act and Trade Marks Act protect the intellectual property in the cyber domain.
NATIONAL CYBER SECURITY POLICY 2013
PURPOSE
v The policy document outlines a road map to create a framework for comprehensive, collaborative and collective response to deal with the issue of cyber security at all levels within the country.
VISION
v To build a secure and resilient cyber space for citizens, businesses and government.
MISSION
v To protect information and information infrastructure in cyberspace, build capacities to prevent and respond to cyber threats, reduce vulnerabilities and Minimize damage from cyber incidents through a combination of institutional structure, people, process, technology and cooperation.
IMPORTANT FEATURES
v To build secure and resilient cyber space.
v Creating a secure cyber ecosystem, generate trust in IT transactions.
v 24 x 7 National Critical Information Infrastructure Protection Center (NCIIPC)
v Indigenous technological solutions(Chinese products and reliance on foreign software should be reduced.)
v Testing of ICT products and certifying them. Validated products
v Creating workforce of 500,000 professionals in the field
v Fiscal Benefits for businessman who accepts standard IT practices, etc.
VARIOUS INSTITUTIONS
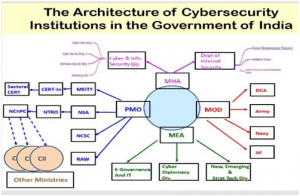
OTHER INITIATIVES
The initiatives taken by the government so far have focused on the issues such as-
1. Cyber security threat perceptions
2. Threats to critical information infrastructure and national security
3. Protection of critical information infrastructure
4. Adoption of relevant security technologies
5. Enabling legal processes
6. Mechanisms for security compliance and enforcement
7. information security awareness
8. Training and research.
THE WAY FORWARD:
- Making threat analysis a norm: Vulnerability report should be generated followed by an audit which will highlight the loopholes in the cyber-attack preparedness of the organisation. An annual review of the software should also be conducted, as and when the software is changed/updated.
- Capacity building: The capacity enhancement for the NCIIPC and CERT-In needs to be undertaken in areas like AI/ML, Blockchain, IoT, Cloud, Automation to address the emerging sophisticated nature of threats and attacks. Sectoral CERTs also have to be set up for many areas including health.
- ‘3-2-1 backup’ approach: Healthcare entities must save 3 copies of each type of data in 2 different formats, including 1 offline. This is an industry best practice to make healthcare institutes cyber secure.
- Enhanced budgetary allocation: A minimum allocation of 0.25% of the annual budget, which can be raised up to 1% to be set aside for cyber security as recommended by the National Cyber Security Strategy. An organisation like AIIMS New Delhi could be counted as a “strategic and public enterprise” as it deals with crores of patients, including the top leadership of the country.
- Crisis Management: For adequate preparation to handle a crisis, cyber security drills can be undertaken which include real-life scenarios with their ramifications. A National Gold Standard should be created, which ensures that Indian hardware and software companies adhere to the highest safety protocols.
- Cyber Diplomacy: On countering cyber-attacks, the cyber security preparedness of key regional blocks like BIMSTEC and Shanghai Cooperation Organisation (SCO) must be ensured via programs, exchanges and industrial support.
- Awareness generation: The general public needs to be made aware of what value their personal data holds or what vulnerabilities it could generate if accessed illegally.
THE CONCLUSION: Cyber-attacks and Ransomware-attacks reflect the still-inadequate protection measures afforded to critical information infrastructure in India. The government needs to step up its data protection efforts through additional measures if it is to prevent such frequent cyberattacks. The absence of awareness of cyber risks among the users and the use of old, legacy technologies are among the factors that add to the vulnerabilities. India also needs to study the evolving tactics, techniques, and procedures (TTPs) of hackers and criminals to be able to prevent these attacks
Mains Practice Questions:
- In the quest for digitalisation, India has become an easy target for cyberattacks due to poor cyber security. Discuss.
- Cyberattacks have connotations for privacy and security and highlight the importance of creating and implementing a national cyber security strategy. Comment.
BACK TO BASICS
TYPES OF CYBERATTACKS: In the current, connected digital landscape, cybercriminals use sophisticated tools to launch cyberattacks against enterprises. Their attack targets include personal computers, computer networks, IT infrastructure and IT systems; some common types of cyberattacks are:
BACKDOOR TROJAN
- A backdoor Trojan creates a backdoor vulnerability in the victim’s system, allowing the attacker to gain remote, and almost total control. Frequently used to link up a group of victims’ computers into a botnet or zombie network, attackers can use the Trojan for other cybercrimes.
CROSS-SITE SCRIPTING (XSS) ATTACK
- XSS attacks insert malicious code into a legitimate website or application script to get a user’s information, often using third-party web resources. Attackers frequently use JavaScript for XSS attacks, but Microsoft VCScript, ActiveX and Adobe Flash can be used, too.
DENIAL-OF-SERVICE (DOS)
- DoS and Distributed denial-of-service (DDoS) attacks flood a system’s resources, overwhelming them and preventing responses to service requests, which reduces the system’s ability to perform. Often, this attack is a setup for another attack.
DNS TUNNELING
- Cybercriminals use DNS tunnelling, a transactional protocol, to exchange application data, like extract data silently or establish a communication channel with an unknown server, such as a command and control (C&C) exchange.
MALWARE
- Malware is malicious software that can render infected systems inoperable. Most malware variants destroy data by deleting or wiping files critical to the operating system’s ability to run.
PHISHING
- Phishing scams attempt to steal users’ credentials or sensitive data like credit card numbers. In this case, scammers send users emails or text messages designed to look as though they’re coming from a legitimate source, using fake hyperlinks.
ZERO-DAY EXPLOIT
- Zero-day exploit attacks take advantage of unknown hardware and software weaknesses. These vulnerabilities can exist for days, months or years before developers learn about the flaws.
SQL INJECTION
- Structured Query Language (SQL) injection attacks embed malicious code in vulnerable applications, yielding backend database query results and performing commands or similar actions that the user didn’t request.
RANSOMWARE
- Ransomware is sophisticated malware that takes advantage of system weaknesses, using strong encryption to hold data or system functionality hostage. Cybercriminals use ransomware to demand payment in exchange for releasing the system. A recent development with ransomware is the add-on of extortion tactics.
JUICE JACKING
- Juice jacking is a security exploit in which an infected USB charging station is used to compromise connected devices. The exploit takes advantage of the fact that a mobile device’s power supply passes over the same USB cable the connected device uses to sync data.
- Juice jacking exploits are a security threat at airports, shopping malls and other public places that provide free charging stations for mobile devices.
BLUEBUGGING
- Bluebugging is a hacking technique that allows individuals to access a device with a discoverable Bluetooth connection. Once the target device accesses a rigged link, the attacker can take full control of it. The hacker can read and send messages, access the victim’s phonebook, and initiate or eavesdrop on phone calls.
- Initially, bluebugging focused on eavesdropping or bugging a computer with Bluetooth capability. With the increasing use of smartphones, cybercriminals shifted to hacking mobile phones. This attack is often limited due to the range of Bluetooth connections, which goes up to only 10 meters.
INTERNATIONAL COMPARISON
India lacks specific provisions in the IT act to tackle cyber-crime. It is more evident when we compare it to the other countries.
|
BASIS |
USA | UNITED KINGDOM |
INDIA |
| INTERCEPTION |
|
|
|
| CHILD PORNOGRAPHY |
|
|
|
| SPAM |
|
|
|
| CYBER TERRORISM |
|
|
|




