TOP 5 TAKKAR NEWS OF THE DAY (1st AUGUST 2023)
1. AKIRA RANSOMWARE
TAG: GS 3: SCIENCE AND TECHNOLOGY AND INTERNAL SECURITY
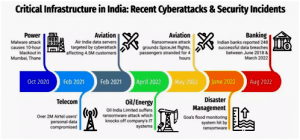
THE CONTEXT: The Computer Emergency Response Team of India issued an alert for ransomware dubbed “Akira.”
EXPLANATION:
- The ransomware targets both Windows and Linux devices, steals and encrypts data, forcing victims to pay double ransom for decryption and recovery.
- The group behind the ransomware has already targeted multiple victims, mainly those located in the U.S., and has an active Akira ransomware leak site with information, including their most recent data leaks.
What is the Akira ransomware?
- It is designed to encrypt data, create a ransomware note and delete Windows Shadow Volume copies on affected devices.
- The ransomware gets its name due to its ability to modify filenames of all encrypted files by appending them with the “.akira” extension.
- The ransomware is designed to close processes or shut down Windows services that may keep it from encrypting files on the affected system.
- It uses VPN services, especially when users have not enabled two-factor authentication, to trick users into downloading malicious files.
- Once the ransomware infects a device and steals/encrypts sensitive data, the group behind the attack extorts the victims into paying a ransom, threatening to release the data on their dark web blog if their demands are not met.
How does Akira ransomware work?
- The ransomware deletes the Windows Shadow Volume copies on the affected device.
- These files are instrumental in ensuring that organisations can back up data used in their applications for day-to-day functioning.
- Each victim is given a unique negotiation password to be entered into the threat actor’s Tor site.
- Unlike other ransomware operations, this negotiation site just includes a chat system that the victim can use to communicate with the ransomware gang, a report from The Bleeping Computer shares.
What is Ransomware?
- Ransomware is a type of malware attack in which the attacker locks and encrypts the victim’s data, important files and then demands a payment to unlock and decrypt the data.
- This type of attack takes advantage of human, system, network, and software vulnerabilities to infect the victim’s device, which can be a computer, printer, smartphone, wearable, point-of-sale (POS)terminal, or other endpoint.
How does ransomware infect devices?
- Ransomware is typically spread through spear phishing emails that contain malicious attachments in the form of archived content files.
- Other methods used to infect devices include drive-by-download, a cyber-attack that unintentionally downloads malicious code onto a device, and specially crafted web links in emails, clicking on which downloads malicious code.
- The ransomware reportedly also spreads through insecure Remote Desktop connections.
Ransomware Attack Examples
WannaCry
- WannaCry is an encrypting ransomware that exploits a vulnerability in the Windows SMB protocol and has a self-propagation mechanism that lets it infect other machines.
- WannaCry is packaged as a dropper, a self-contained program that extracts the encryption/decryption application, files containing encryption keys, and the Tor communication program.
Cerber
- Cerber is ransomware-as-a-service (RaaS) and is available for use by cybercriminals, who carry out attacks and spread their loot with the malware developer.
- Cerber runs silently while it is encrypting files and may try to prevent antivirus and Windows security features from running to prevent users from restoring the system.
NotPetya and Petya
- Petya is ransomware that infects a machine and encrypts an entire hard drive by accessing the Master File Table (MFT).
- This makes the entire disk inaccessible, although the actual files are not encrypted. Petya was first seen in 2016 and was spread mainly through a fake job application message linking to an infected file stored in Dropbox. It only affected Windows computers.
- Petya requires the user to agree to give it permission to make admin-level changes. After the user agrees, it reboots the computer, and shows a fake system crash screen while it starts encrypting the disk behind the scenes. It then shows the ransom notice.
Source: https://www.thehindu.com/sci-tech/technology/what-is-the-akira-ransomware/article67134462.ece
2. PRADHAN MANTRI AWAS YOJANA – URBAN (PMAY-U)
TAG: GS 2: SOCIAL JUSTICE
THE CONTEXT: A total of 75.51 lakh houses have been completed, out of which 71.39 lakh have been occupied till now under the Prime Minister’s Awas Yojana (PMAY-U), the Centre’s flagship programme to provide housing to the urban poor.
EXPLANATION:
- Minister for Housing and Urban Affairs informed the Rajya Sabha that Uttar Pradesh had the largest number of houses completed, and Gujarat and Andhra Pradesh were other high-performing states.
- The release of central assistance is incumbent upon the fulfilment of mandatory compliances by the concerned States and UTs.
- This includes the submission of Utilization Certificates (UCs) for central assistance released earlier, commensurate physical progress and Aadhaar seeding of beneficiaries in the Management Information System (MIS).
Pradhan Mantri Awas Yojana (Urban) Programme
- It is a flagship Mission of the Government, which is implemented by the Ministry of Housing and Urban Affairs (MoHUA). It was launched in 2015.
- The mission aimed to address the urban housing shortage among the economically backward sections, including the slum dwellers, by ensuring a ‘pucca’ house to all eligible urban households by the year 2022.
- The scheme period though, has now been extended up to December 2024 in order to complete all the houses sanctioned without changing the funding pattern and implementation methodology.
Beneficiaries
- The mission seeks to address the housing requirement of urban poor, including slum dwellers.
- Beneficiaries include Economically weaker sections (EWS), low-income groups (LIGs) and Middle Income Groups (MIGs).
- The annual income cap is up to Rs 3 lakh for EWS, Rs 3-6 lakh for LIG and Rs 6 + -18 lakhs for MIG. The EWS category of beneficiaries is eligible for assistance in all four verticals of the Missions, whereas LIG and MIG categories are eligible under only Credit linked subsidy scheme (CLSS) component of the Mission.
- For identification as an EWS or LIG beneficiary under the scheme, an individual loan applicant will submit a self-certificate/ affidavit as proof of income.
- A beneficiary family will comprise a husband, wife, unmarried sons and/or unmarried daughters.
- The beneficiary family should not own a pucca house either in his/her name or in the name of any member of his/her family in any part of India to be eligible to receive central assistance under the mission.
- The ownership of houses is provided in the name of the female member or in a joint name.
- Preference is also given to differently-abled persons, senior citizens, SCs, STs, OBCs, Minorities, single women, transgender and other weaker & vulnerable sections of society.
- All eligible beneficiaries under all components of the scheme should have an Aadhaar/ Aadhaar Virtual ID which should be integrated with the details of beneficiaries
Scope:
- The Mission covers the entire urban area consisting of Statutory Towns, Notified Planning Areas, Development Authorities, Special Area Development Authorities, Industrial Development Authorities or any such authority under State legislation which is entrusted with the functions of urban planning & regulations.
- The mission will be implemented as Centrally Sponsored Scheme (CSS) except for the component of credit-linked subsidy, which will be implemented as a Central Sector Scheme.
Implementation Methodology
- The Mission will be implemented through four verticals giving options to beneficiaries, ULBs and State Governments. These four verticals are as below.
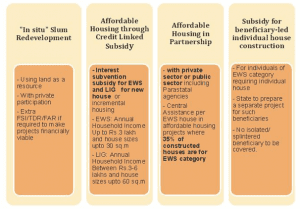
Affordable Rental Housing Complexes (ARHCs)
- Ministry of Housing & Urban Affairs has initiated Affordable Rental Housing Complexes (ARHCs), a sub-scheme under Pradhan Mantri Awas Yojana – Urban (PMAY-U).
- This will provide ease of living to urban migrants/ poor in the Industrial Sector as well as in the non-formal urban economy to get access to dignified, affordable rental housing close to their workplace.
- Beneficiaries for ARHCs are urban migrants/ poor from EWS/ LIG categories.
- ARHCs will be a mix of single/double bedroom Dwelling Units and Dormitory of 4/6 beds, including all common facilities, which will be exclusively used for rental housing for a minimum period of 25 years.
3. CORPORATE DEBT MARKET DEVELOPMENT FUND (CDMDF)
TAG: GS 3: ECONOMY
THE CONTEXT: The Union government has approved a scheme providing complete guarantee cover for debt raised by the Corporate Debt Market Development Fund (CDMDF), a backstop facility for investment-grade corporate debt.
EXPLANATION:
- SEBI released guidelines for investment by mutual fund schemes and asset management companies in CDMDF units.
Guarantee Scheme for Corporate Debt (GSCD):
- This scheme aims to provide a safety net for the Corporate Debt Market Development Fund (CDMDF), established under SEBI Regulations, and facilitate investments in corporate debt securities.
- The scheme, managed by the Guarantee Fund for Corporate Debt (GFCD), seeks to stabilize markets and foster investor confidence.
- It operates as a Trust Fund formed by the DEA, Ministry of Finance, and is managed by the National Credit Guarantee Trustee Company Ltd. (NCGTC).
Purpose of the Scheme
- The primary objective of the Guarantee Scheme for Corporate Debt (GSCD) is to offer a 100% guarantee cover against debt raised or to be raised by the Corporate Debt Market Development Fund (CDMDF) during market dislocation.
- By providing this safety net, the government aims to instil confidence in investors, thereby stabilizing the corporate debt market and fostering economic growth.
- The guarantee extends to the principal amount, interest accrued, and other bank charges up to a limit of Rs. 30,000 crore.
Corporate Debt Market Development Fund (CDMDF)
- The CDMDF is a fund wherein the corpus of Rs 3000 crore will be created by contributions from the fixed-income schemes of mutual funds and asset management companies
- The government will provide a guarantee of up to Rs 30,000 crore additionally.
- In times of market dislocation and drying up of liquidity in secondary markets, the CDMDF can buy investment-grade corporate bonds of up to 5-year maturity from the mutual funds to the extent of the enlarged corpus.
Access to the fund
- The respective mutual funds shall have access to sell corporate debt securities during market dislocation, held in the portfolio of contributing schemes, to the CDMDF.
- Access to the fund shall be in proportion to the contribution made to the Fund at a mutual fund level (i.e., in the ratio of total units of CDMDF held by all specified debt schemes of each mutual fund).
Key benefits
- The CDMDF will become a lender of last resort to mutual funds and enable them to meet redemptions in extraordinary times when there is little or no secondary market liquidity in the corporate bond market.
- CDMDF, an alternative investment fund, will act as a backstop for the purchase of investment-grade corporate debt securities.
- It will enhance secondary market liquidity by creating a permanent institutional framework for activation in times of market stress. The fund will be launched by Finance Minister.
- During normal times, CDMDF will deal in low-duration government securities (G-sec), treasury bills, tri-party repo on G-secs, and guaranteed corporate bond repo with a maturity not exceeding seven days.
- Corporate debt securities to be bought by CDMDF during market dislocation include listed money market instruments, for which the long-term rating of issuers will be considered, Sebi said.
- CDMDF will buy only investment-grade securities from secondary markets, listed and having residual maturity of up to five years. 1It will not buy any unlisted, below-investment-grade or defaulted debt securities or securities in respect of which there is a material possibility of default or adverse credit news or views.
4. AMOUNT OF PLASTIC EXCEEDING THE GLOBAL WASTE MANAGEMENT CAPACITY AS PER PLASTIC OVEERSHOOT DAY REPORT 2023.
TAG: GS 3: SCIENCE AND TECHNOLOGY
THE CONTEXT: Earth saw its first Plastic Overshoot Day on July 28, 2023.
Plastic Overshoot is the point at which the amount of plastic exceeds the global waste management capacity.
EXPLANATION:
- Swiss-based research consultancy Earth Action (EA), published The Plastic Overshoot Day Report 2023.
- Swiss-based research consultancy Earth Action (EA), pointed out that nearly 68,642,999 tonnes of additional plastic waste will end up in nature this year.
- India is among the 12 countries, along with China, Brazil, Indonesia, Thailand, Russia, Mexico, the United States, Saudia Arabia, the Democratic Republic of Congo, Iran, and Kazakhstan, which are responsible for 52 per cent of the world’s mismanaged plastic waste.
- Increased production of plastics will lead to global plastics pollution tripling by 2040.
- The report pointed out that 159 million tonnes of plastics are to be produced globally in 2023, and 43 per cent (68.5 million tonnes) will end up causing pollution.
- Plastic Overshoot Day sheds light on a critical aspect of the world’s plastic consumption: Short-life plastics, encompassing plastic packaging and single-use plastics.
- These categories account for approximately 37 per cent of the total plastic commercialised annually.
- According to the report, three countries (followed by India) with the highest mismanaged waste are Mozambique, Nigeria and Kenya, all belonging to Africa.
- According to Delhi-based think tank Centre for Science and Environment (CSE) report, The Plastic Life Cycle, India recycles 12.3 per cent of its plastic waste and incinerates 20 per cent.
- Ministry of Environment, Forests and Climate Change also suggest India has a cumulative capacity to process 14.2 million tonnes of plastic waste annually.
- This includes recycling and incineration, indicating that the country has the capacity to process 71 per cent of all the primary plastic that is produced.
GOVERNMENT POLICIES
The Plastic Waste Management Rules, 2016 aim to:
- Increase the minimum thickness of plastic carry bags from 40 to 50 microns and stipulate a minimum thickness of 50 microns for plastic sheets.
- Expand the jurisdiction of applicability from the municipal area to rural areas because plastic has reached rural areas also.
- To bring in the responsibilities of producers and generators.
- To introduce a collection of plastic waste management fees through pre-registration of the producers, importers of plastic carry bags/multilayered packaging and vendors selling the same for establishing the waste management system.
- To promote the use of plastic waste for road construction as per Indian Road Congress guidelines or energy recovery, or waste to oil etc., for gainful utilization of waste.
The Plastic Waste Management Rules, 2021 aim to:
- The Ministry of Environment, Forest and Climate Change, Government of India, has notified the Plastic Waste Management Amendment Rules, 2021.
- It did not override 2016 rules and subsumed its provisions.
- Littered plastic impacts adversely on both terrestrial and aquatic ecosystems.
- The rules prohibit identified single-use plastic items which have low utility and high littering potential by 2022.
- The manufacture, import, stocking, distribution, sale and use of the following single-use plastic, including polystyrene and expanded polystyrene, commodities shall be prohibited with effect from the 1st of July 2022: –
- earbuds with plastic sticks, plastic sticks for balloons, plastic flags, candy sticks, ice-cream sticks, and polystyrene [Thermocol] for decoration.
- plates, cups, glasses, cutlery such as forks, spoons, knives, straws, trays, wrapping or packing films around sweet boxes, invitation cards, cigarette packets, plastic or PVC banners less than 100 microns, stirrers.
- In order to stop littering due to lightweight plastic carry bags, the thickness of plastic carry bags has been increased from fifty microns to seventy-five microns and to one hundred and twenty microns with effect from the 31st of December 2022.
- This will also allow reuse of plastic carry due to increase in thickness.
MITIGATION:
- To mitigate plastic pollution, India must Invest in waste management policies like Extended producer responsibility (EPR).
- Plastics that are not designed for circular use must be phased out.
- India was among the few countries in 2019 to propose a global ban on single-use plastics.
- The idea was later widened, and the world agreed in March 2022 to draw up a global treaty on plastic pollution by 2024.
- The UN Plastic Treaty represents a once-in-a-lifetime opportunity to spark global action against plastic pollution.
5. CELL FREE DNA (cfDNA): A USEFUL TOOL TO UNDERSTAND HUMAN DISEASES.
TAG: GS 3: SCIENCE AND TECHNOLOGY
THE CONTEXT: The world is increasingly finding cfDNA to be a useful tool to understand human diseases and to use the knowledge to improve diagnosis, monitoring, and prognosis.
EXPLANATION:
- In the human body, most of the DNA in a genome is neatly packed inside cells with the help of specific proteins, protecting it from being degraded.
- Some fragments of DNA are ‘released’ from their containers and are present outside the cell in the body fluids.
- These small fragments of nucleic acids are widely known as cell-free DNA (cfDNA).
- Scientists have been aware of degraded fragments of nucleic acids in body fluids since 1948.
- Since genome sequencing technologies started to become more accessible.
CELL FREE DNA (cfDNA)
- cfDNA can be generated and released from a cell in several possible situations:
- When a cell is dying, the nucleic acids become degraded.
- An array of processes modulates the degradation; the amount, size, and source of the cfDNA can vary across a range as well.
- The release of cfDNA could occur together with a variety of processes, including those required for normal development, those related to the development of certain cancers, and those associated with several other diseases.
- One of the initial reports of the levels of cfDNA in diseases came from studies that were taking a closer look at an autoimmune disease: systemic lupus erythematosus – where the body’s own immune system attacks specific cells.
APPLICATIONS OF cfDNA:
Non-Invasive Prenatal Testing:
- cfDNA has been widely used in screening foetuses for specific chromosomal abnormalities, an application known as non-invasive prenatal testing.
- The application stems from one of the first reports of cfDNA in pregnancies, published in The Lancet in August 1997.
- The availability of affordable genome-sequencing approaches will allow clinicians to sequence cfDNA fragments that correspond to foetal DNA.
- They can then use it to understand specific chromosomal abnormalities that involve changes in the chromosomal copy number.
- Such changes can lead to conditions like Down’s syndrome, which is due to a change in chromosome 21 (there are three copies of chromosome 21 in place of two, so it is also called trisomy 21).
- cfDNA-based technique helps clinicians to screen mothers from a few millilitres of blood obtained after nine or ten weeks of pregnancy to ensure the developing foetus is devoid of such chromosomal abnormalities.
- The test is almost 99% accurate for trisomy 21 or Down’s syndrome and a bit less so for other common trisomies (of chromosomes 13 and 18).
- Earlier screening for such abnormalities would have entailed inserting a fine needle into the body to retrieve the amniotic fluid and cells covering the developing foetus lab, which carried risks to both the foetus and the mother.
Diagnosis and Treatment of Cancers:
- The application of cfDNA is the early detection, diagnosis, and treatment of cancers.
- Researchers at the Johns Hopkins Kimmel Cancer Centre, Maryland, reported developing a new test they have dubbed ‘Genome-wide Mutational Incidence for Non-Invasive Detection of Cancer’, or ‘GEMINI’.
- They adopted a whole-genome-sequencing approach to cfDNA extracted from patients.
- They examined a type of genetic mutation, when combined with machine-learning approaches, that could provide a way to detect cancer early.
- Using a particular machine-learning model, some genomic data, and data from a computed tomography (CT) scan, the researchers have successfully detected lung cancer, including those with early-stage disease, in more than the 90% of the 89 people they studied.
- They found that combining the new approach with the existing approaches could significantly enhance their ability to detect cancers early.
- The researchers also identified seven individuals who did not have cancer but had a high chance of developing it – and subsequently did so 231 to 1,868 days after the initial test.
- The team’s findings were published in the journal Nature Genetics.
Other Applications:
There are several emerging applications of cfDNA:
- Understanding of a body rejecting a transplanted organ.
- Some cfDNA obtained from the donor who is donating the organ called donor-derived cfDNA, dd-cfDNA could provide an early yet accurate estimate of how well the organ is being taken up.
- This is an attractive proposition because changes in the levels of cfDNA in the blood would precede any biochemical or molecular markers that researchers currently use as a proxy for organ acceptance.
- cfDNA could send a signal earlier than other markers if something is going to go wrong.
- cfDNA could be used as a biomarker for neurological disorders like Alzheimer’s disease, neuronal tumours, stroke, traumatic brain injury, and even metabolic disorders like type-2 diabetes and non-alcoholic fatty liver disease.
In a true sense, cfDNA genomics promises to set us on the path of more effective disease screening and early diagnosis and on course for a healthy world.


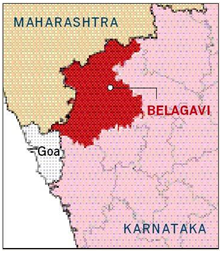 lines. In 1957, unhappy with the demarcation of boundaries, Maharashtra demanded realignment of its border with Karnataka.
lines. In 1957, unhappy with the demarcation of boundaries, Maharashtra demanded realignment of its border with Karnataka.